The U.S. Department of Defense and private individuals pumping the Alfa Bank hoax also assisted former Special Counsel Robert Mueller’s investigation into Donald Trump for supposed collusion with Russia, newly discovered documents suggest.
The Georgia Tech researchers embroiled in the Alfa Bank hoax prepared white papers for the U.S. Department of Defense about the Democratic National Committee hack and created a “Mueller List” on the Russian intelligence agency hackers, the newly obtained documents indicate. The white papers were prepared for the Defense Advanced Research Projects Agency (DARPA), a section of the U.S. Department of Defense.
A recent dump of documents from Georgia Tech reveals that explosive detail and several other facts connected to the continuing special counsel investigation into Spygate. Here’s a rundown.
White Papers for the U.S. Department of Defense
Last month, The Federalist first reported that Special Counsel John Durham’s team asked lead Georgia Tech researcher Manos Antonakakis: “‘Do you believe that DARPA should be instructing you to investigate the origins of a hacker (Guccifer_2.0) that hacked a political entity (DNC)?’” Antonakakis responded that that was a question for the DARPA director, an implied acknowledgment that yes, DARPA had asked him to investigate the hack.
In response, DARPA’s chief of communications denied any involvement “in efforts to attribute the DNC hack.” “Dr. Antonakakis worked on DARPA’s Enhanced Attribution program, which did not involve analysis of the DNC hack,” DARPA spokesman Jared Adams told the Washington Examiner. Adams further told the Washington Examiner that “DARPA was not involved in efforts to attribute the Guccifer 2.0 persona, nor any involvement in efforts to attribute the origin of leaked emails provided to Wikileaks.”
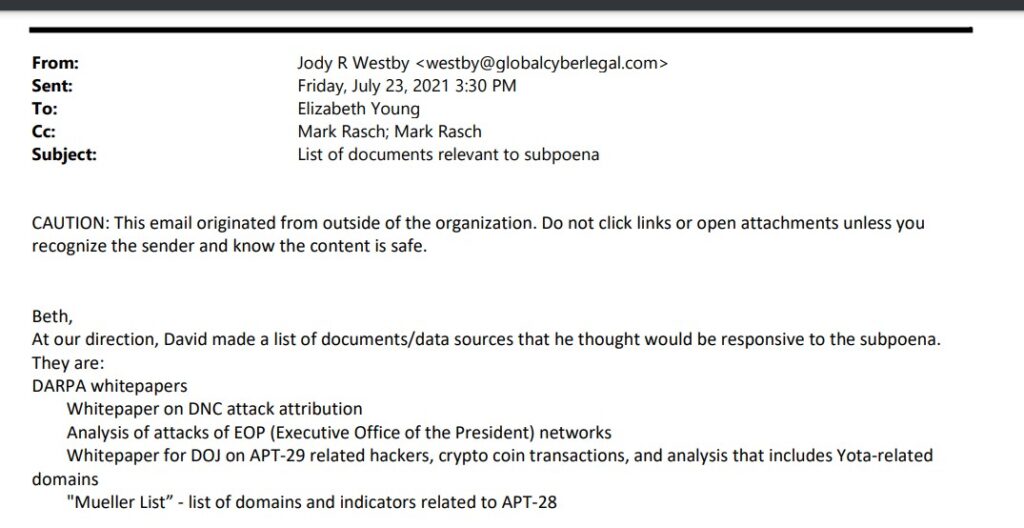
But now an email obtained by The Federalist indicates Georgia Tech researchers drafted a series of white papers for DARPA, including on the “DNC attack attribution,” and on what they called a “Mueller List” of “domains and indicators related” to DNC hackers.
The email dated July 23, 2021 followed Durham dropping a second subpoena on Georgia Tech for more documents related to its investigation of the Alfa Bank hoax and other related issues. (More on that subpoena below). In that email, a lawyer representing David Dagon, the second Georgia Tech researcher involved in the Alfa Bank hoax who also worked on the DARPA Enhanced Attribution program, shared a list of “documents/data sources” Dagon believed would be responsive to the subpoena of Georgia Tech documents.
Listed under the heading of “DARPA whitepapers” were four documents, including “Whitepaper on DNC attack attribution”; Analysis of attacks of EOP (Executive Office of the President) networks”; “Whitepaper for DOJ on APT-29 related hackers, crypto coin transactions, and analysis that includes Yota-related domains”; and “‘Mueller List’—list of domains and indicator related to APT-28.”
Of these DARPA whitepapers, the first and fourth both relate to the DNC hack, with the final paper also connecting to the Mueller investigation. APT-28 is the more formal name for the Russian intelligence group of hackers known colloquially as Fancy Bear. As part of his investigation, Mueller charged 12 Russian intelligence agents allegedly working as Fancy Bear with crimes related to the DNC hack.
This email represents the latest evidence suggesting Georgia Tech and DARPA assisted in the DNC hack investigation and Mueller’s investigation, notwithstanding DARPA’s strident denials.
Yota-Related Domains
The above email raises a second question worth probing, namely whether tech executive Rodney Joffe used the whitepaper Georgia Tech researchers prepared for DARPA on “Yota-related domains” in his continued attempt to frame Trump as colluding with Russia.
As I explained earlier this week, in February 2017, Michael Sussmann, allegedly on behalf of Joffe, presented the CIA four files of data purporting to show the use of the Russian-made Yotaphone near Trump. The Yotaphone supposedly traveled with Trump to Michigan and later to the Executive Office of the President during the presidential transition period.
The Yotaphone hoax, as I detailed, represents a huge scandal because it involved both the exploitation of sensitive data related to the EOP and the apparent physical (or electronic) surveillance of Trump. Further, the data provided to the CIA was deceptive by omission and peddled to trigger a CIA investigation of the sitting president of the United States of America.
But the above email now adds to the scandal the possibility that the DARPA-funded research on the Yota domains was shared with Joffe or other outsiders, who then used that intel to track the Russian-based Yotaphones to create the conspiracy theory later peddled to the CIA. This potential scenario needs further investigation.
Georgia Tech Gave Mueller a Large File of Trump-Related Material That Went Missing
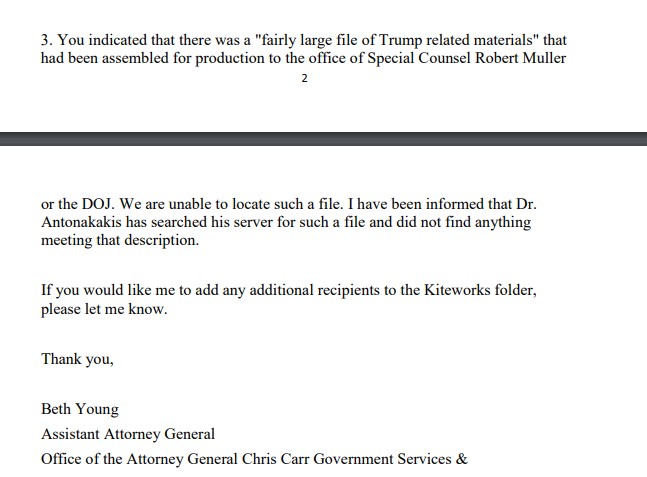
That the Georgia Tech researchers worked with Mueller’s investigation into Trump also seems clear from an exchange between lead prosecutor Andrew DeFilippis and the Georgia Attorney General’s Office, which represented Georgia Tech in its response to the subpoena. In that email thread, the attorney representing Georgia Tech noted that DeFilippis had “indicated that there was a ‘fairly large file of Trump related materials’ that had been assembled for production to the office of Special Counsel Robert [Mueller] or the DOJ.”
“We are unable to locate such a file,” the email continued, even though “Dr. Antonakakis has searched his server for such a file and did not find anything meeting that description.”
Whether the “fairly large file of Trump related materials” was ever found is unknown.
Durham Is Digging Far and Wide
The most recent Georgia Tech documents also reveal the breadth and scope of the potential conspiracies Durham is investigating, with a subpoena from July 2021 to Georgia Tech and its related organization seeking documents related to “a purported secret communications channel between the Trump Organization, Spectrum Health, and the Russian Bank Alfa Bank,” as well as material related to “the purported presence or use of Russian-made Yotaphones by or in the vicinity of Donald Trump or individuals affiliated with Donald Trump.”
Significantly, the subpoena also sought “all documents, records, and information” related to the Alfa Bank and Yotaphone research, including work conducted under or pursuant to contracts with DARPA.

The Georgia Tech documents also reveal that this subpoena is the second served on the university by the special counsel’s office, with the first issued in fall 2020, according to another email. (One wonders what the original subpoena sought and what put the investigators onto the Alfa Bank and Yotaphone trail.) Emails released also indicate that the special counsel’s office subpoenaed documents from Dagon.
Immunity for Dagon
Emails included in the Right-to-Know release from Georgia Tech also provide more texture to the Durham case against Sussmann, who is currently awaiting trial next month on a charge that he lied to the now-former FBI General Counsel James Baker in providing Baker data and white papers purporting to establish the Trump-Alfa Bank secret communication network.
Last Friday, in response to Sussmann’s claim that Durham should be required to provide Joffe immunity so the tech executive would testify on Susssmann’s behalf, the special counsel noted that to date it had only immunized one witness—Dagon. The special counsel noted that it granted Dagon immunity on July 28, 2021, “because, among other reasons, at least five other witnesses who conducted work relating to the [Alfa Bank] allegations invoked (or indicated their intent to invoke) their right against self-incrimination.”
The documents reviewed by The Federalist show that, as of July 26, 2021, Dagon was “en route to DC for his meeting with the Special Counsel and testimony with the Grand Jury,” meaning the immunity grant came late in the day for Dagon. Another email from Dagon’s attorney to Georgia Tech noted that “David Dagon was given full statutory immunity by the Special Counsel in its investigation.”
“He has been cooperating and working with the Special Counsel’s team and testified before the Grand Jury on three days,” Dagon’s attorney Jody Westby told the Georgia Tech legal team, in the context of requesting payment from the university for the legal services Westby and her team performed on behalf of Dagon.
That Dagon testified for three days before the grand jury suggests the special counsel’s team had quite a few questions to ask the cyber researcher. From another email, it seems likely that, whatever Dagon said, he convinced the special counsel’s office that Antonakakis was not involved in any criminal activity. On July 29, 2021, Antonakakis’ attorney Mark Schamel emailed DeFilippis, noting that now that the special counsel has “appropriately categorized Dr. Antonakakis as a witness,” they would happily discuss a follow-up meeting with Durham’s team.
Georgia Tech Entered a Joint Defense Agreement—Until It Didn’t
Another fascinating detail contained in the Georgia Tech dump concerned the apparent joint defense agreement the individuals ensnared in the Alfa Bank hoax initially entered into with each other. A “joint-defense agreement” is where parties agree to exchange confidential information and work together, typically, but not always, in relation to a criminal investigation. When parties have entered a joint-defense agreement, they may share information and communications with each other, without the communications losing the protection of attorney-client privilege.
After the special counsel dropped its second subpoena on Georgia Tech, Dagon’s attorney emailed a lawyer at Georgia Tech, noting that Dagon would not be responding to the subpoena served on Georgia Tech—that was solely Georgia Tech’s responsibility. Dagon’s attorney then added: “We have never seen the first subpoena Georgia Tech produced or your production; nor have we seen this second subpoena. Although Georgia Tech agreed to an informal joint defense agreement, after we produced our subpoena and relevant documents, Georgia Tech pulled back from that and refused to share any information, . . . We are also not privy to your discussions with the Special Counsel office.”
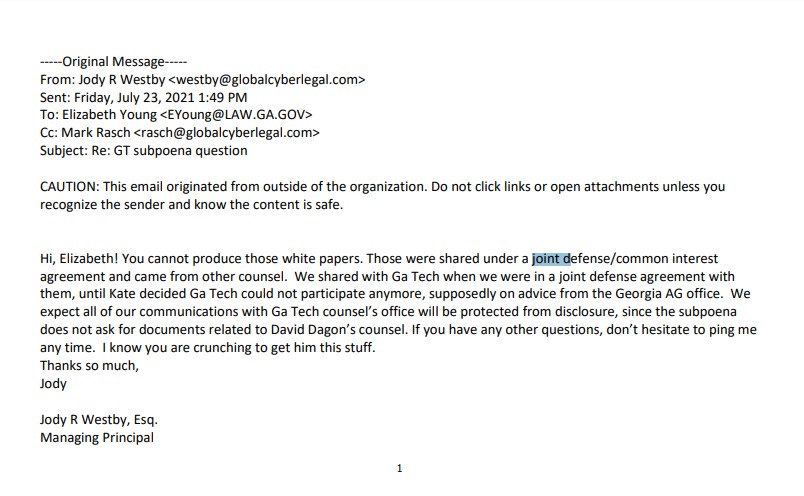
A few days later, Dagon’s attorney provided more background when she emailed the Georgia attorney general’s office, noting that Georgia Tech “cannot produce those white papers,” in reference to three white papers Dagon’s lawyer had provided Georgia Tech’s lawyer in September 2020.
Those white papers, Dagon’s lawyer noted, “were shared under a joint defense/common interest agreement and came from other counsel.” “We shared them with Ga Tech when we were in a joint defense agreement with them, until [Georgia Tech’s lawyer] decided Ga Tech could not participate anymore, supposedly on advice from the Georgia AG office,” Dagon’s attorney snarked.
This exchange suggests that Georgia Tech, in addition to having entered into a joint defense agreement with Dagon, had entered into one with another of the players involved in the Alfa Bank hoax, although which one is unknown.
Also of interest is that Dagon’s attorney noted that she expects “all of our communications with GA Tech counsel’s office will be protected from disclosure, since the subpoena does not ask for documents related to David Dagon’s counsel.” The question, then, is whether special counsel Durham ever saw those three white papers or ever followed up with a subpoena for communications with Dagon’s attorney. If not, he may want to do so now.